User access review is a control to periodically verify that only legitimate users have access to applications or infrastructure. During a user access review, an application business or IT owner may discover that users who left the enterprise or transferred to another team in the enterprise continue to have access to applications or infrastructure after their access credentials or privileges should have been removed. This vulnerability can be exploited, resulting in financial and/or reputational loss to the enterprise. However, following some best practices that allow full transparency and ensure that unauthorized users do not have access to an application or system can help mitigate this risk.
User Types
A user is a person who uses an application or tool to achieve a desired business outcome. In the IT world, users can be classified into two broad groups:
- Business users—They use an application or tool as part of achieving their defined business outcome. Some examples are finance application users who use an application for enterprise finance activity and product development application users who use an application for a product development process.
- IT users—They have access to an application, tool or system for their assigned application delivery responsibilities, such as application development, testing, deployment or operations support. This user type is usually given access based on IT team type, such as development, support or general.
Common User Access Risk Scenarios
The following are some common user access risk scenarios that result in users who can access applications or systems to which they should not have access:
- Users leave a team but still have one or more of their previous team access privileges.
- Users change roles but still have one or more of their previous role access privileges.
- Users leave the enterprise but still have one or more access privileges.
- A user’s reporting manager is involved in approving user continued access attestation. The risk occurs when a current reporting manager moves to a different team/assignment, but the extract used for attestation communication is not appropriately changed and such communication is sent to the user’s previous reporting manager.
User Access Review Best Practices
Implementing user access review best practices can help to eliminate or avoid the mentioned risk scenarios.
Business User Access Review Best Practices
The application business owner is responsible for the effectiveness of the user access review control for business users. The owner can assign a delegate to assist with this activity, but the application business owner remains accountable for this control and any violations.
Best practices that application business owners can implement to help ensure effective user access reviews include:
- When a new business user joins the team, the application business owner attests and provides relevant roles and access levels for the business user.
- When a business user leaves the team or changes roles, the application business owner validates the user and the user’s access level for any updates or removal.
- At predetermined intervals (prescheduled part of calendar of activity), a business user access review is automatically triggered or manually initiated. The application business owner receives a list of existing business users, roles and access privileges. The application business owner then takes action to remove or change any incorrect privileges.
- Any change to the application business owner and/or delegate is to be updated as part of transition from current contact to new contact.
IT User Access Review Best Practices
IT users need to have access to the application back end to execute their responsibilities. IT users’ access privileges are dependent on their team and role.
The application’s IT owner is responsible for the effectiveness of the user access review control for IT users. The owner can assign a delegate to assist with this activity, but the application’s IT owner remains accountable for this control and any violations. The IT owner is the custodian of the business data. Therefore, after the IT owner completes the access review, he or she must get approval from the application business owner to complete the user access review cycle.
If the application business owner is not an IT expert, the application IT owner can set up a clarification session with the business owner to explain the application and the IT responsibilities. This effort can increase trust between the business team and the IT team and result in a more productive workplace, as improved trust enhances speed and reduces cost.
Best practices that an application’s IT owners can implement to help ensure effective user access reviews include:
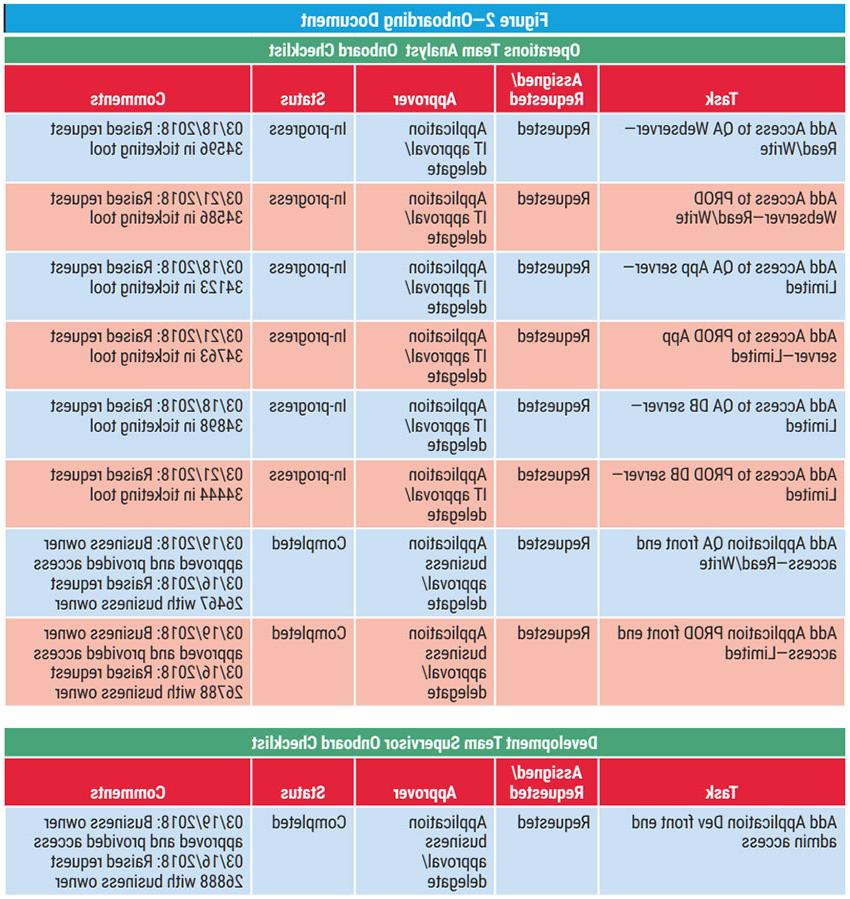
- Developing an onboarding template (figure 1) that provides the user roles, the tasks for each role and the required access for each task. The onboarding template role responsibilities are based on the segregation of duties (SoD) control (figure 2). The SoD assigns responsibilities and privileges for IT team members so that no single person can introduce fraudulent or malicious code without detection. No user can have access that can potentially compromise the control. For example, for change management, a developer produces code and performs unit testing. A lead then verifies the code and test results and moves the code to a higher environment. The developer cannot move the code to a higher environment, and the lead does not have the ability to develop code.
- Making it mandatory to use an onboarding document when providing access privileges to a user
- Using a calendar of activity (figure 3) to mark and initiate periodic user access reviews as part of the enterprise audit and assurance program. Determine the frequency of user access reviews based on the criticality of the asset, the associated risk and user movement dynamics.
- Based on the calendar of activity, automatically triggering or manually initiating IT user access review activity
- Using an offboarding document (figure 4) when a user moves out of a role, team or enterprise to remove user access to tools and applications. The review should be scheduled as close as possible to the actual time of the offboarding. Ensuring accurate offboarding means eliminating risk due to unauthorized users.
- Developing automated processes for onboarding and offboarding. For example, an onboarding script processes access requests or adds access for various systems and tools based on the SoD. An offboarding script processes access removal requests or access removal from various systems and tools (see figures 5 and 6).
- If collaborative tools, such as SharePoint or Webex, are being used and access is requested for users outside of the team(s), assigning an administrator to validate access requests. As part of this assurance, a periodic automatic workflow of access verification and action retention or removal that is based on the request response of yes or no should be configured.
- Reflecting reporting changes holistically. If the user’s reporting manager is involved in user attestation and this communication is received by the user’s previous reporting manager, manual intervention, including follow-ups, is necessary.





Conclusion
During this time of rapid transformation of how IT and business teams work, enterprises expect security to not be compromised for the speed of delivery. The new DevSecOps culture promises secure, high-quality software faster and implies that security is the underlying core consideration through the IT process. Enterprises need to challenge themselves to improve access review by using automation tools and techniques. By adhering to the disciplines discussed previously, enterprises can assure concerned stakeholders that all is well with respect to user access.
Sundaresan Ramaseshan, CISM, ITIL Foundation, ITIL Service Operation
Is an IT supervisor supporting security tools at Ford Motor Private Ltd. in Chennai, India. He has more than 27 years of experience in various IT software development life cycle roles. Ramaseshan continues to enhance his depth of knowledge in the security domain and share some of the successes he observes in day-to-day operations in the hopes that they may benefit the IT security community.
